Why Windows 11 25H2 Became Larger: Security Changes Explained Without Marketing
-
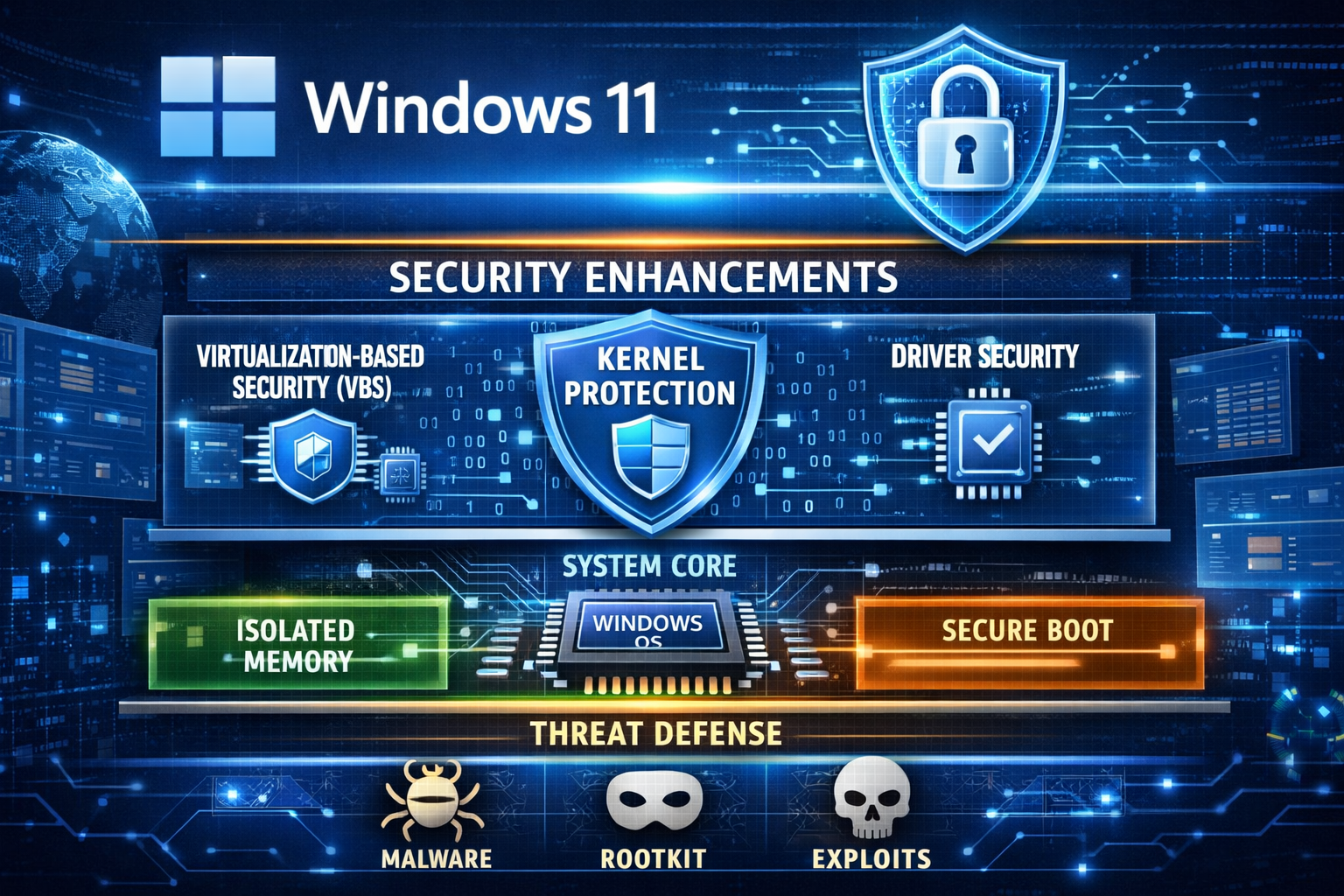 Windows 11 25H2 became noticeably larger in size, and Microsoft recently explained why. The reason is not new visual features or bundled apps, but a significant expansion of security mechanisms at the system and kernel level.
Windows 11 25H2 became noticeably larger in size, and Microsoft recently explained why. The reason is not new visual features or bundled apps, but a significant expansion of security mechanisms at the system and kernel level.The key point is that Microsoft strengthened protection in areas that operate at the lowest level of the operating system: the kernel, drivers, and memory isolation. These changes are expensive in terms of disk space, but they are intentional.
One of the main additions is deeper kernel-level protection. This targets modern attack vectors such as rootkits, malicious drivers, and exploits that attempt to load before or alongside the OS. To achieve this, Windows now ships with more built-in components, validation data, and fallback mechanisms. These are not downloaded on demand — they are stored locally to ensure reliability and offline patching.
Another major factor is the expanded use of Virtualization-Based Security (VBS) and HVCI. In simple terms, parts of Windows are now isolated in a protected virtual environment. Even if malicious code executes, it cannot easily reach critical system components. This requires additional system images, memory maps, and compatibility layers, which directly increases the size of the OS image and cumulative updates.
Driver security has also been tightened. Windows 11 25H2 includes stricter driver validation, larger blocklists for vulnerable drivers, and more integrity-checking data. This is particularly important because many real-world exploits rely on legitimate but insecure drivers to gain kernel access.
A common question is whether these security mechanisms affect gaming performance.
In most modern gaming scenarios, the impact is minimal to negligible. On current CPUs, especially mid-range and high-end systems, the overhead introduced by VBS and kernel protections is usually within the margin of error — often a few percent at most, and frequently unnoticeable in GPU-bound games.
However, there are edge cases. Competitive players chasing maximum FPS in CPU-limited titles, or users on older hardware, may observe small drops in minimum FPS or slightly higher latency. This is why some gamers choose to disable features like VBS or Memory Integrity.
Disabling these protections can indeed recover a small amount of performance, but it comes with real trade-offs. Turning them off reduces protection against kernel-level malware, malicious drivers, and advanced persistence techniques. These attacks are rare for casual users, but they are exactly the type used in targeted attacks, cheat loaders, and advanced malware.
In other words, disabling these features does not make Windows “unsafe” overnight, but it does lower the security ceiling. The system becomes more similar to older Windows versions in terms of attack surface.
The increase in Windows 11 25H2 size is therefore not accidental and not a sign of unnecessary bloat. It reflects a strategic decision by Microsoft to prioritize system integrity, offline reliability, and long-term security, even at the cost of larger update packages and higher storage requirements.
Whether to keep all these protections enabled depends on the user. For most systems, especially general-purpose and gaming PCs with modern hardware, the default configuration offers a reasonable balance between security and performance.
-

Why Some Gamers Disable VBS in Windows 11 — And When It Actually Makes Sense
Speaking as an experienced Windows and PC gaming user, the topic of disabling VBS (Virtualization-Based Security) comes up regularly, and it’s worth explaining it without extremes or fear-mongering.Some gamers disable VBS not because they are “against security”, but because they are chasing very specific performance goals. This usually applies to competitive or CPU-bound scenarios: high-refresh-rate esports titles, older engines, simulation games, or systems where the CPU is already the limiting factor.
VBS introduces an additional isolation layer between the operating system and critical components like memory and the kernel. On modern CPUs, the overhead is generally small, but it is real. In certain edge cases, this can slightly reduce minimum FPS, increase frametime variance, or add small latency penalties. For most users, this difference is barely noticeable. For competitive players, even a few percent can matter.
Another reason is hardware context. On older CPUs or entry-level systems, virtualization-based features can be proportionally heavier. In those cases, disabling VBS may produce a more noticeable improvement than on modern high-end hardware.
That said, it is important to understand what is being traded away.
Disabling VBS lowers protection against kernel-level attacks, malicious or vulnerable drivers, and advanced persistence techniques. These are not common threats for average home users, but they are the exact mechanisms used by sophisticated malware, cheat loaders, and targeted attacks. With VBS off, Windows behaves closer to older security models.
This does not mean the system becomes instantly unsafe. Windows still has multiple layers of defense. However, the security margin is reduced, especially against low-level threats that traditional antivirus solutions are not always effective against.
So when is disabling VBS a reasonable choice?
It can make sense for:
- Competitive gamers who prioritize maximum and consistent FPS
- Users with older CPUs where virtualization overhead is more pronounced
- Controlled environments where software sources are trusted and limited
When is it not recommended?
- General-purpose systems
- PCs used for work, browsing, downloads, or mixed workloads
- Systems exposed to unknown drivers, mods, or untrusted software
In short, disabling VBS is not a “magic performance tweak” and not something that should be done blindly. It is a calculated trade-off. For most modern gaming PCs, leaving it enabled provides better overall balance. For niche performance-focused scenarios, disabling it can be justified — as long as the user understands the risks.

